What is Steganography?
The term “steganography” originates from the Greek words steganos (meaning “covered” or “hidden”) and graphein (meaning “to write” or “to draw”). It refers to the technique of concealing messages within other non-secret files such as images, videos, or audio files.
Beyond simple data hiding, steganography also serves to protect copyright and prevent unauthorized use of digital content. It’s common to encrypt the hidden message before embedding it to enhance confidentiality.
Key Concepts and Workflow
Steganography typically involves the following components:
Message Data: The confidential information to be hidden. There’s no restriction on the file type, but the message must be equal to or smaller in size than the cover data. Compression is often used to reduce its size.
Cover Data: The file in which the message is hidden. Common formats include images, videos, or audio. It should be larger or at least the same size as the message.
Stego Key: A secret key used during the embedding process. Only those who possess the key can extract and read the hidden message.
Stego Data: The final output file that contains the hidden message. Ideally, the stego data should appear visually or structurally identical to the original cover data.
Requirements for Steganography
Imperceptibility: The embedded message must not be detectable by third parties during transmission.
Transparency: The stego data must maintain high fidelity and remain unaffected by external stimuli.
Robustness: The message must survive typical data processing techniques such as compression or minor file modifications.
Security: Only authorized individuals with the correct key can detect and extract the hidden message, and the method must resist statistical or brute-force attacks.
✅ The larger and more complex the cover data—and the smaller the message—the better the quality and stealthiness of steganography.
Procedure
🔐 Embedding Phase
- Compress the message.
- Encrypt it using an encryption key.
- Hide it in the cover data using a stego key.
- Resulting stego data should appear unchanged to the human eye.
🔓 Extraction Phase
- Use the stego key to extract the hidden message from the stego data.
- Decrypt the extracted data.
- Decompress it to recover the original message.
Types of Steganography
📂 Pure Steganography
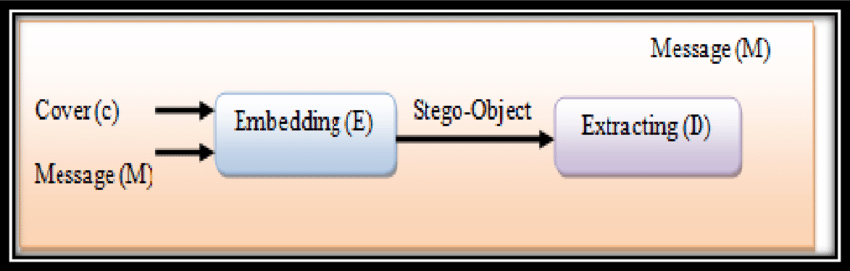
- No use of stego keys; relies solely on secret embedding/extraction algorithms.
- Sender and receiver don’t share any keys or prior information.
- If the method is exposed, the message becomes vulnerable to unauthorized extraction.
🔑 Secret-Key Steganography
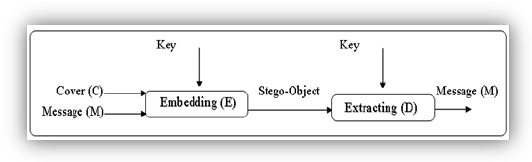
- Uses the same secret key for both embedding and extraction.
- Key must be pre-shared between sender and receiver.
- Vulnerable if the shared key is leaked.
🗝️ Public-Key Steganography
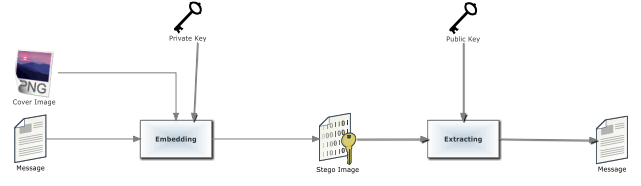
- Uses a public key for embedding and a private key for extraction.
- No need to share keys beforehand.
- Only the receiver with the private key can extract the message.
- If the private key is leaked, the security is compromised.
Steganography Algorithms
There’s a trade-off between the size of the hidden message and the invisibility of the stego file.
1. Spatial Domain Insertion
- Embeds the message directly into spatial or temporal data (e.g., images, audio).
- Simple and fast with larger capacity.
- Vulnerable to compression and file modifications.
2. Frequency Domain Insertion
- Uses human perceptual properties to hide data in high-frequency domains.
- Common algorithms:
- DCT: Discrete Cosine Transform
- DFT: Discrete Fourier Transform
- Wavelet: Wavelet Transform
- More robust but complex and slower, with less capacity.
🎯 LSB (Least Significant Bit) Algorithm
- Replaces the least significant bit of each byte in a pixel with message bits.
- Chosen because changing LSBs has the least visual impact.
🧠 Issues:
- If message bits are inserted linearly, statistical analysis can detect anomalies.
- May create visual artifacts in some cases.
🔎 Solution: Selected LSB
- Embed bits only in one color channel (e.g., red, green, or blue).
- Adjust upper bits slightly to maintain color fidelity.
✅ This improves stealth and minimizes visual distortion while allowing more data to be hidden.